
Security in FPGA-based Systems: Digital circuit design typically involves a Field-Programmable Gate Array (FPGA), which is made up of memory, programmable logic gates, and other parts.
In the same way that Application-Specific Integrated Circuit (ASIC) configuration is done, hardware description languages (HDLs), such as VHDL and Verilog, are frequently used to describe FPGA settings.
Numerous consumer products, including cameras, cellphones, driverless vehicles, image and video processing, and security systems, can utilize FPGA security.
FPGAs are widely employed in many corporate settings, including servers, medical electronics, and military hardware.
A well-designed FPGA has certain built-in safety precautions. Fundamentally, an FPGA is less transparent than a standard central processing unit (CPU).
Processors need to have a well-documented instruction set, data pipeline, and memory architecture to create code and software that runs efficiently.
The possibility of security lapses has increased along with the development of FPGA-based devices. Data theft, system failures, and even the loss of life can result from security breaches.
So, a key component of FPGA-based systems is design security.
Threats to Security in FPGA-based Systems

Overview of FPGA security threats
Threats to FPGA-based systems, intellectual property theft (IP), and major data loss are all connected to this FPGA device.
For every assault, a different level of security is required. The primary FPGA security attacks can be divided into the following categories.
 Cloning Attacks
Cloning Attacks
- During cloning, attackers replicate FPGA development programming. After that, they apply the bitstream to a similar device and sell it under their name. Cloning can encompass everything or only a section of the FPGA design.
- For instance, there can be limitations imposed by the seller on the purchased cores. It is the most prevalent national security issue in a volatile FPGA.
 Overbuilding
Overbuilding
- Overbuilding could lead to an unreliable foundry producing more FPGA chips than necessary and selling them to system developers at a lower price.
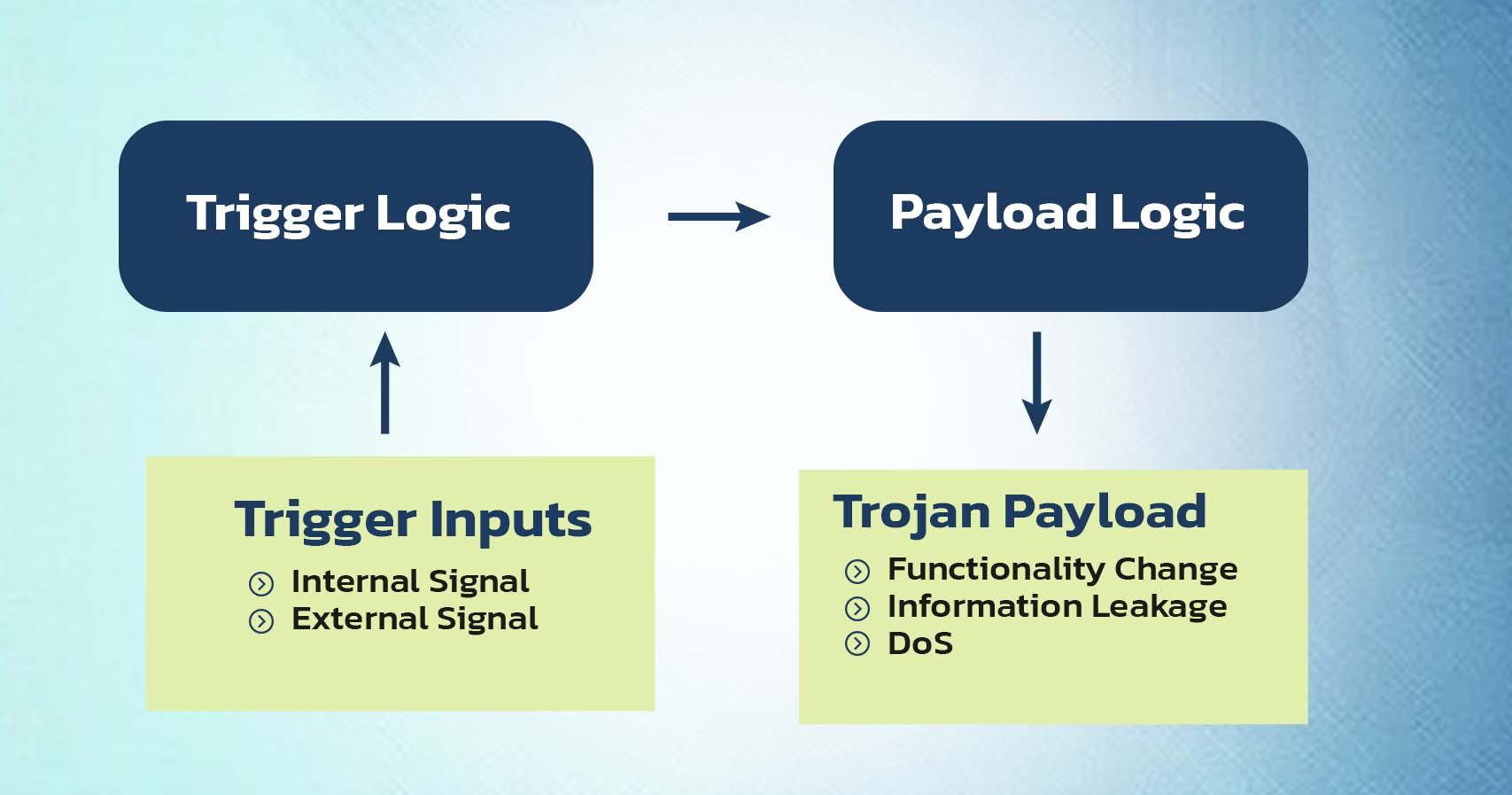
 Hardware Trojans
Hardware Trojans
- Trojans are designed to alter physical circuits and alter how a system functions. They compromise the dependability of hardware, lead to system failures, provide users remote access to devices, and endanger the security of sensitive data.
Side-Channel Attacks

- Cybercriminals use side-channel assaults instead of traditional techniques to gain access to the FPGA. Instead, they use the system’s informational patterns against it.
- When a system employs encryption, the physical data that is made available is used in side-channel attacks. For instance, side-channel attacks can reveal the keys stored in the FPGA chips when a bitstream file is encrypted, which is supported by the majority of FPGA vendors, rendering the bitstream vulnerable.
- One of the most frequent side-channel attacks is fault injection. Hackers may build controllable weaknesses to modify the FPGA after introducing mistakes to test the system’s response.
- Voltage, timing, and laser errors are used in these assaults. The hacker often has to be nearby or in physical control of the device to detect these informational patterns.
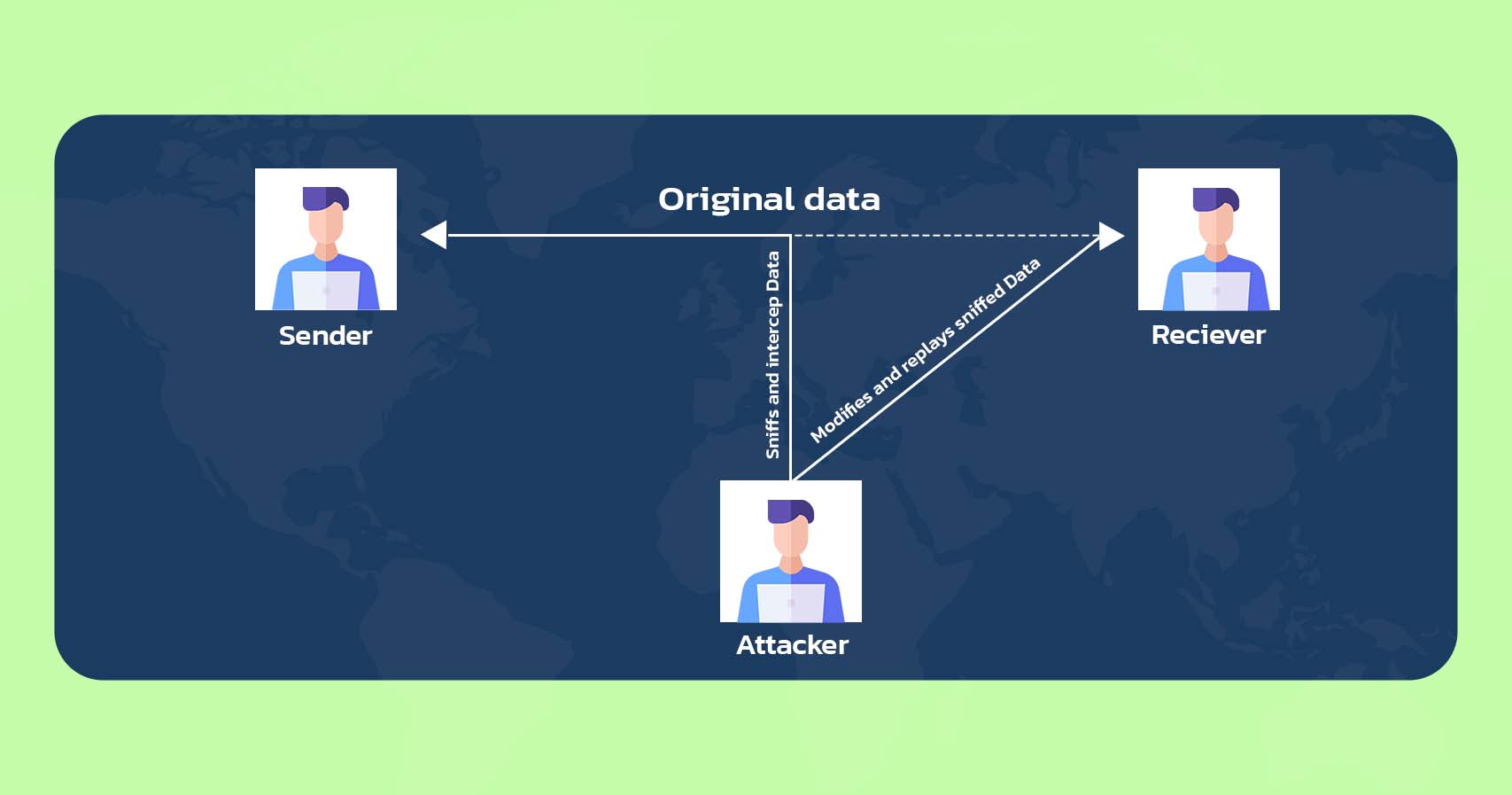
Replay Attacks

- The FPGA replay attack, which includes a hacker downgrading an FPGA-based system to a previous version with known weaknesses, poses a significant security and privacy risk for FPGA architecture.
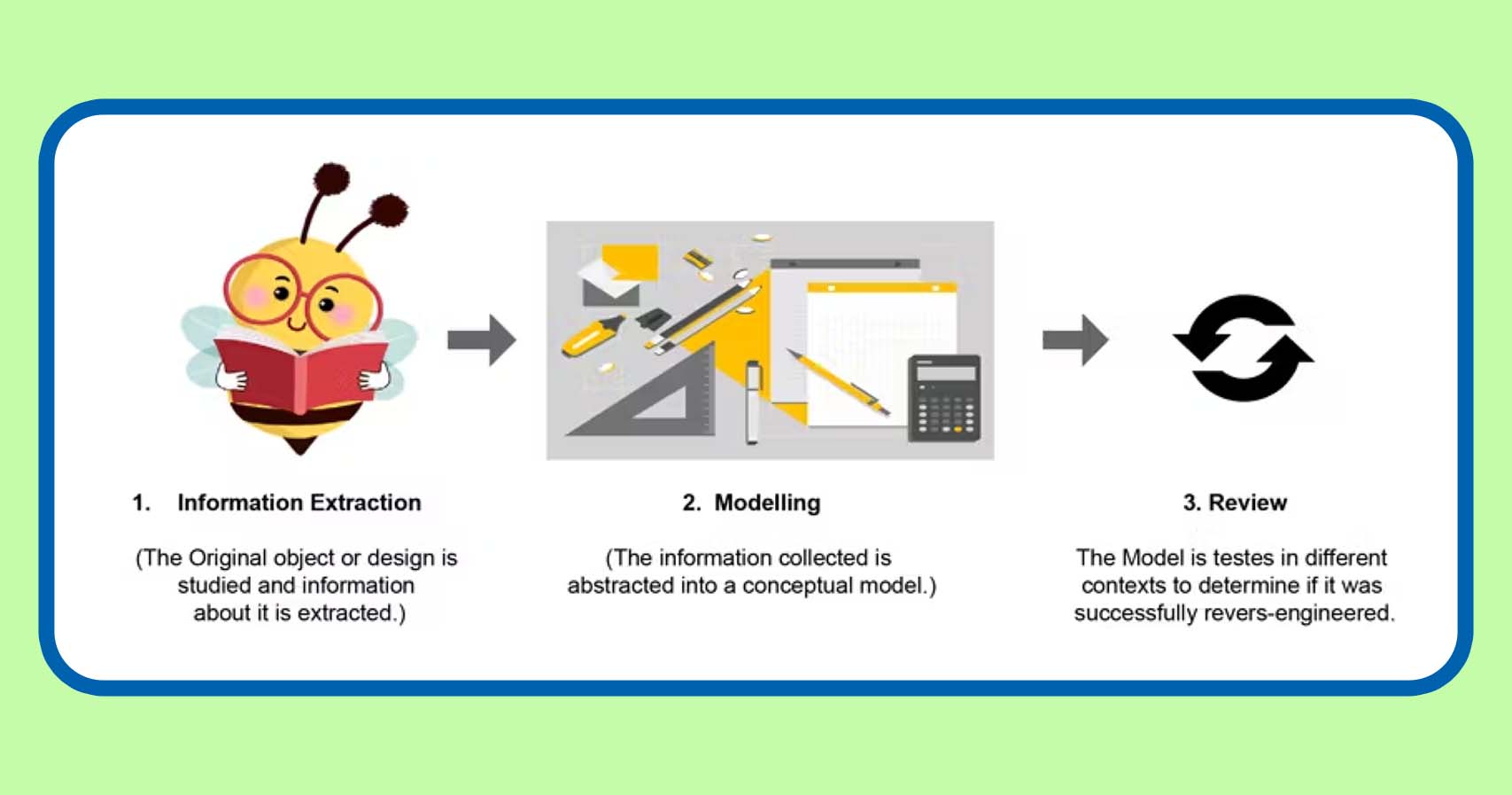
 Reverse Engineering
Reverse Engineering
- The two fundamental types of IC reverse engineering are gate-level netlist reverse engineering and reverse engineering employing image processing.
- Through the use of gate-level netlist reverse engineering techniques, such as register-transfer-level (RTL) or structure-level description, adversaries can derive higher-level functionality from the gate-level netlist.
- Hackers can use reverse-engineering techniques to further examine the FPGA after intercepting the bitstream. For operations like recovering circuit designs and bitstream bit mapping, there are tools made just for the job.
- Reverse engineering all or a portion of a bitstream involves stealing intellectual property from the authors, even though it isn’t technically hacking.
Spoofing
- During spoofing, the attacker’s bitstream is switched out for the original FPGA bitstream. That bitstream might include components that were created by cloning or reverse engineering. Because of this, the system can become exposed, giving hackers full control of the device.
- In some safety-critical applications, such behavior could result in injuries or deaths caused either directly or indirectly by the hacker’s actions. If the bitstream could be accessed remotely, there would be a serious security issue.
Tampering

- Attackers who tamper with applications change their architecture. The attacker can alter the application’s logic to leak data or disable specific functionality.
- Tampering is also called reverse engineering because it requires changing values in the bitstream.
Bitstream Interception

- One of the most popular ways for attackers to affect FPGAs is through bitstream interception. Numerous documents exist for this security flaw.
- In terms of vulnerabilities, getting a hold of those vital configuration files opens a can of worms. In addition to using other techniques, hackers can use files to acquire control and steal bitstream data.
- The bitstream is one of this puzzle’s most crucial elements. Criminals are free to cause mayhem once they get it. Hackers usually require physical access to the device to retrieve the bitstream.
Thermal Laser Stimulation
- For fault analysis, thermal laser stimulation (TLS) is frequently utilized. To retrieve confidential information, such as the key for bitstream decoding, this technique can also be used to identify and read a chip’s memory contents. Whether this attack technique defeats modern ICs with software composition analysis (SCA) defenses has not yet been shown.
- TLS attacks necessitate expensive hardware and extraordinarily slow execution durations (a qualified microscope for failure analysis is required for this type of attack).
- However, given that the attack can be executed even when the component is not powered, producers of programmable logic devices cannot afford to ignore this category of attacks.
Countermeasures to Security Threats in FPGA-based Systems

Due to its reprogrammable nature, which can allow for unauthorized access, modification, and exploitation, FPGA-based systems are vulnerable to a variety of system security concerns.
Here are various defensive layers against security risks in FPGA-based systems.
Secure design: In the early stages of design, security should be taken into account. Vulnerabilities in the FPGA design tools need to be examined, and remedial action needs to be taken.
Encryption: In FPGA- based systems, encryption can be employed to safeguard the confidentiality and integrity of the data. Both the data contained in the FPGA and the communication between the FPGA and other components can be encrypted.
Access control: To restrict access to the FPGA and its resources, access control measures can be implemented. Ensure that only authorized users can access the FPGA, this may entail establishing user authentication, role-based access control, and other security measures.
Hardware security: A hardware-based security system can be utilized to defend the FPGA from intrusions. These defenses might consist of hardware-based encryption, secure boot, and tamper-resistant packaging.
Firmware Protection: The FPGA’s firmware needs to be shielded from unwanted access or change. This can be done by putting firmware encryption, digital signatures, and other safeguards in place to make sure the firmware is genuine and valid.
Continuous monitoring: The FPGA-based system may be continuously monitored to aid in the real-time detection and mitigation of security threats. This can involve keeping an eye out for unusual behavior on the system, installing intrusion detection systems, and taking additional steps to identify and address security incidents.
Conclusion

Security in FPGA-based systems is a crucial issue that needs to be addressed to guarantee the integrity and confidentiality of sensitive data.
Injection of malicious code, side-channel attacks, reverse engineering, and manipulation are just a few security risks that FPGA-based systems are susceptible to.
Access control techniques, encryption, and authentication are just a few of the countermeasures that can be used to lessen these risks.
Physical security measures can also be implemented, such as using tamper-proof packaging and safe storage facilities.
In conclusion, to reduce current threats and foresee future ones, the security of FPGA-based systems necessitates a holistic approach that incorporates both hardware and software solutions.
Organizations may guarantee the integrity and confidentiality of their data and guard against potential breaches by putting the right security measures in place.



 Cloning Attacks
Cloning Attacks  Overbuilding
Overbuilding  Hardware Trojans
Hardware Trojans 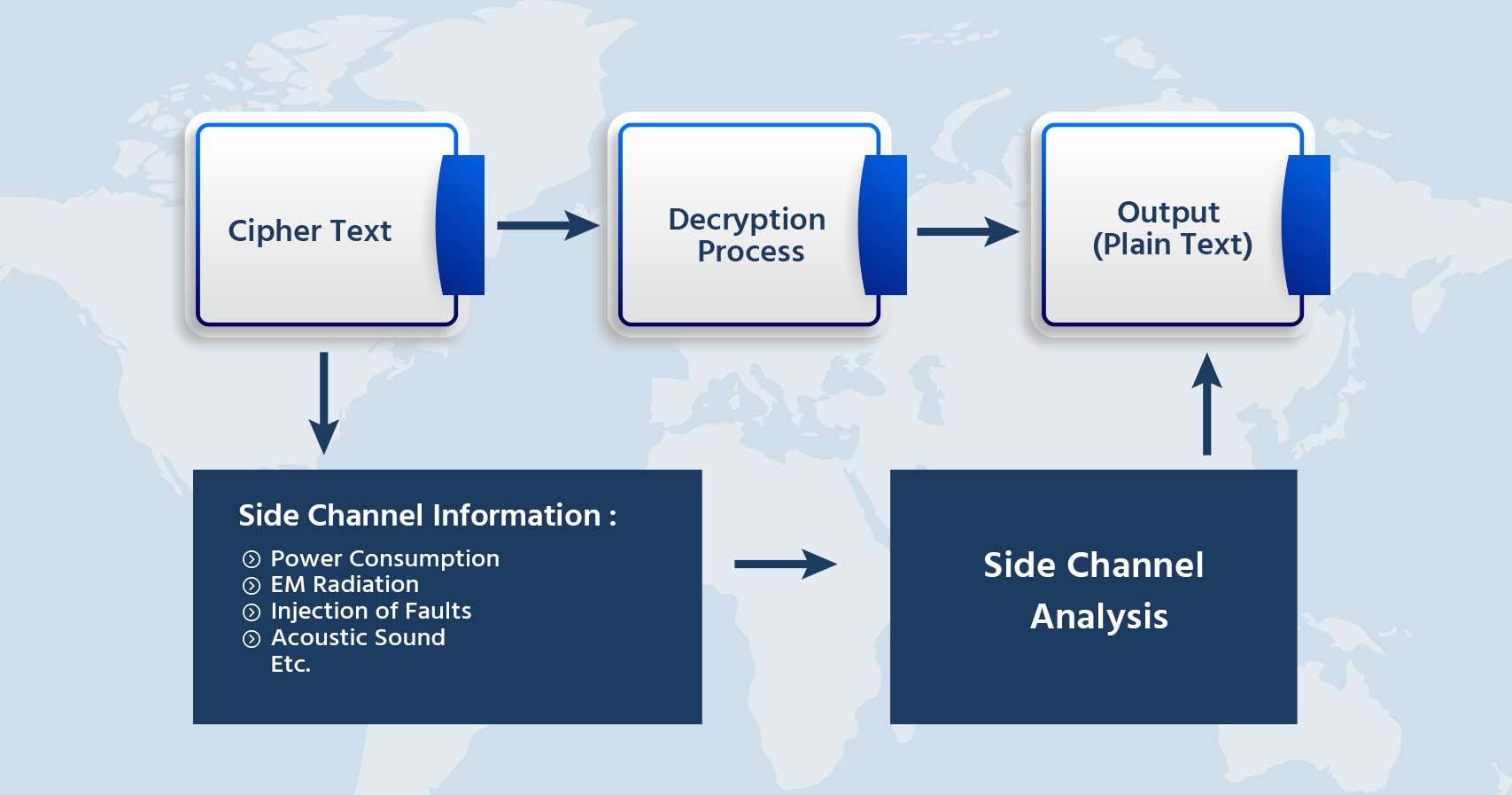
 Reverse Engineering
Reverse Engineering 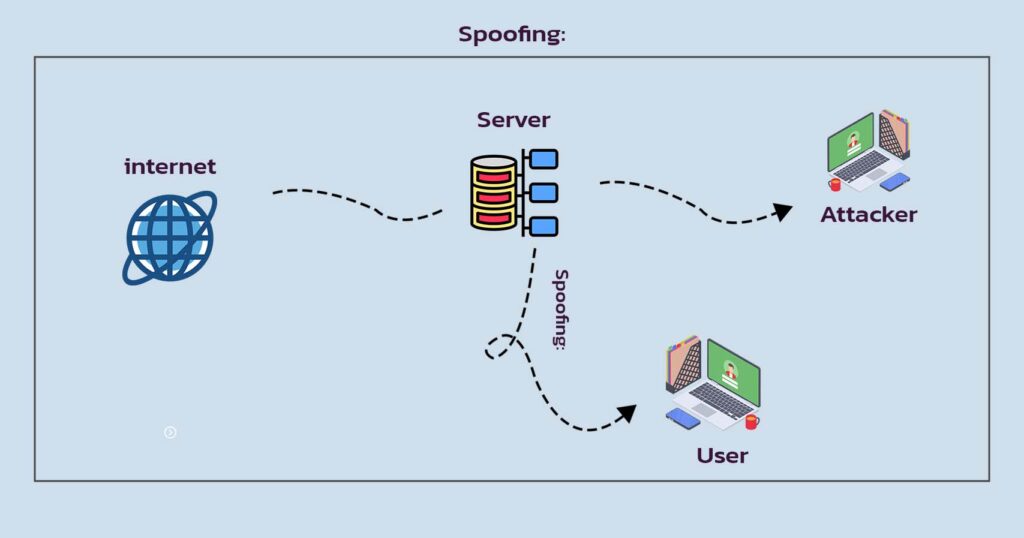


![Advanced Driver Assistance System [ADAS] Everything You Needs to Know](https://www.logic-fruit.com/wp-content/uploads/2022/10/Advanced-driver-assistance-systems-Thumbnail.jpg)





