In the realm of cybersecurity, the Trusted Platform Module (TPM) stands as a crucial yet often enigmatic technology. TPM is a hardware-based security solution designed to safeguard computing devices, protect critical functions, and ensure data integrity. It plays a pivotal role in securing modern digital systems against various threats.
This overview will demystify TPM, covering its definition, historical evolution, components, features, and vital role in the ever-evolving landscape of cybersecurity.
TPM Overview
1. Trusted Platform Module (TPM) is a hardware-based security solution that provides secure storage of sensitive data, cryptographic keys, and measurement of system integrity.
2. TPM is a chip that is embedded in a computer’s motherboard or other hardware components.
3. Some key features and characteristics of TPM include:
- Secure storage of keys and passwords
- Platform integrity measurement
- Remote attestation for security verification
- Protected input and output of sensitive data
4. Differences between TPM and other security technologies
- TPM differs from other security technologies, such as software-based encryption and firewalls, in that it is hardware-based and provides a higher level of security. TPM works with software and firmware to provide enhanced security in various applications and systems.
TPM Applications

Trusted Platform Module (TPM) has a wide range of applications in various industries and organizations. Here are some examples:
- Secure boot: TPM can verify the integrity of the system boot process and prevent the loading of unauthorized code or malware.
- Disk encryption: TPM can be used to securely store encryption keys for full disk encryption, preventing unauthorized access to sensitive data.
- Digital signatures: TPM can generate and securely store private keys for digital signatures, providing an added layer of security for electronic transactions and document signing.
- Virtual private networks (VPNs): TPM can be used to authenticate users and encrypt communication between remote endpoints in VPNs.
- Cloud computing: TPM can help secure data and applications in cloud computing environments by providing secure storage and key management.
1. Industries and organizations that use TPM for security purposes include:
- Financial institutions
- Healthcare providers
- Government agencies
- Cloud service providers
- Automotive manufacturers
- Aerospace and defense companies
2. By using TPM, these organizations can enhance security and protect against cyber attacks, data breaches, and other security threats.
TPM Standards
Trusted Platform Module (TPM) has various standards and specifications that define its functionality and interoperability. Some of these standards include:
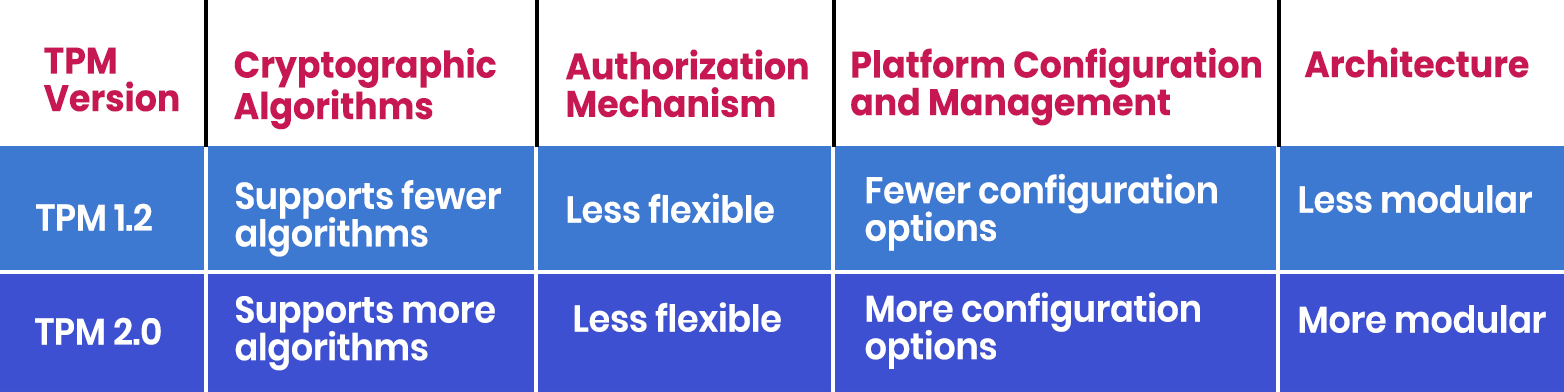
- Trusted Computing Group (TCG) TPM 1.2 Specification: This is the original TPM specification released by TCG in 2003. TPM 1.2 provides a set of commands for key management, storage, and platform integrity measurement.
- TCG TPM 2.0 Specification: This is the latest version of the TPM specification released in 2014. TPM 2.0 includes enhancements such as new cryptographic algorithms, enhanced authorization mechanisms, and improved command response codes.
The differences between TPM 1.2 and TPM 2.0 include:
- TPM standards help ensure interoperability and security by providing a common framework for TPM implementation and ensuring that different TPMs can work together seamlessly.
- TPM standards also help ensure that TPMs meet specific security requirements and are tested for compliance with the standards.
Configuring TPM on the system
1. Install the TPM driver
- You will need to install the TPM driver for your Ubuntu Linux OS. You can install the necessary packages using the following command in the terminal:
sudo apt-get install tpm-tools libtss2-dev
- This will install the TPM tools and libtss2-dev packages, which provide the necessary tools and libraries to interact with the TPM.
2. Check if TPM is detected
- After installing the TPM driver, you can check if the TPM is detected by running the following command in the terminal:
sudo tpm_version
- This will display information about the TPM version and status.
3. Enable the TPM in the BIOS
- You will need to enable the TPM in the BIOS settings of your SBC. This will vary depending on your SBC’s BIOS but typically involves navigating to the Security or TPM menu and selecting the option to enable the TPM.
4. Configure the TPM
- Once the TPM is enabled, you can configure it for your Ubuntu Linux OS. You can do this by modifying the /etc/init.d/tpm-tools file to include the appropriate settings for your system.
- For example, you might need to specify the device file location and security policies.
5. Test the TPM
- After configuring the TPM, you can test that it is working properly by running the following command in the terminal:
sudo tpm2_getrandom 20
- This will generate 20 random bytes using the TPM.
6. Integrate the TPM with your software
- Once the TPM is tested and working, you can integrate it with your software. This involves modifying your software to use TPM-specific functions and APIs to interact with the TPM.
- For example, you might use the TPM to store cryptographic keys or to sign and verify data.
7. Develop TPM-specific applications
- You can also develop applications that specifically use the TPM, such as secure boot loaders or critical management tools. These applications will require additional programming to communicate with the TPM and use its functions.
Examples of TPM Commands

1. Initialize the TPM
- This one-time process sets up the TPM and generates the necessary keys. You can do this by running the following command:
sudo tpm2_startup -c
- This command will initialize the TPM and clear any existing keys
2. Create a new key
- After initializing the TPM, you can create a new key to use for securing data or authenticating users. You can do this by running the following command:
sudo tpm2_createprimary -C o -g sha256 -G rsa -c primary.ctx
- This command will create a new primary key and store it in the file primary. ctx. You can use this key to create other keys, such as a key for encrypting data or a key for signing messages.
3. Use the key
- Once you have created a key, you can use it to secure data or authenticate users. For example, you can use the key to encrypt a file by running the following command:
sudo tpm2_encryptdecrypt -c primary.ctx -I input.txt -o output.txt
- This command will use the primary key stored in the primary. ctx to encrypt the file input.txt and store the result in output.txt.
Conclusion
In a digital world rife with threats, the Trusted Platform Module (TPM) stands as a stalwart guardian of security and trust. From its hardware-based foundation to its multifaceted applications, TPM plays a pivotal role in securing our computing environments.
As TPM continues to evolve and adapt to emerging challenges, its importance in bolstering cybersecurity remains undeniable. It is the bedrock upon which we build trust in our digital interactions, protecting our data, systems, and privacy in an increasingly interconnected world.





![Advanced Driver Assistance System [ADAS] Everything You Needs to Know](https://www.logic-fruit.com/wp-content/uploads/2022/10/Advanced-driver-assistance-systems-Thumbnail.jpg)





